Featured
Why That Security Training From 2015 Won't Save You From Today's Modern Phishing
UK Withdrawal from the Internet in 2025.
Privacy Engineering in a Post AI World
Sealed with a Quish - the Problem with Cybersecurity Terminology
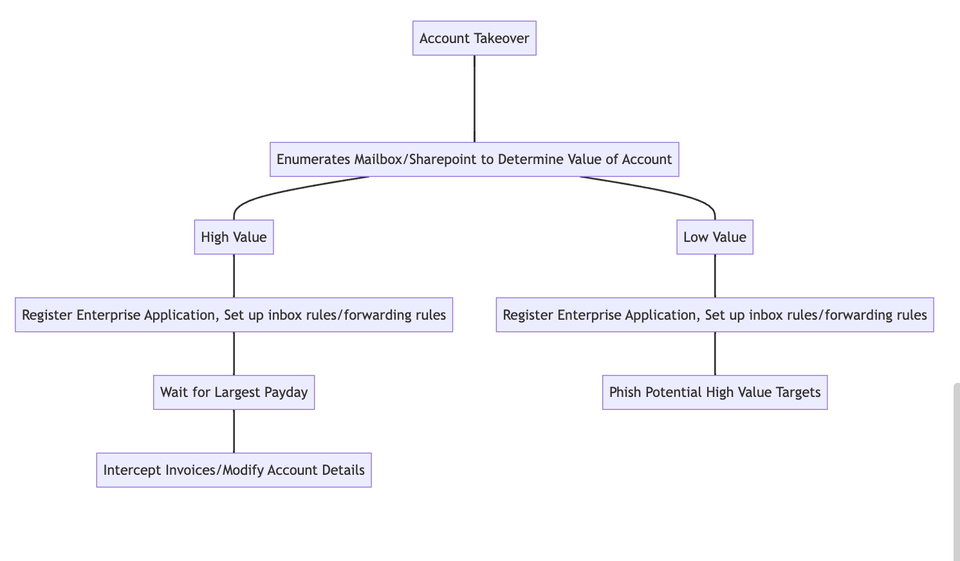
Seven Essential Strategies to Prevent and Detect Business Email Compromise
The Hidden Privacy Risk in Commercial VPN Services: Root Certificate Installation
Next.js Vulnerability - CVE-2025-29927
BSides London 2024
Yubikey Vulnerability - How Bad Is It?
Should I be using AI in my business?
We need to talk about your backups
Blog
-
Log4j - Has your business been affected? What next?
-
We need to talk about your backups
-
Should I be using AI in my business?
-
Yubikey Vulnerability - How Bad Is It?
-
BSides London 2024
News
-
We need to talk about your backups
-
Next.js Vulnerability - CVE-2025-29927
-
The Hidden Privacy Risk in Commercial VPN Services: Root Certificate Installation
-
Seven Essential Strategies to Prevent and Detect Business Email Compromise
-
Privacy Engineering in a Post AI World