Why That Security Training From 2015 Won't Save You From Today's Modern Phishing
Remember when phishing emails were laughably obvious? The Nigerian prince with questionable grammar, the "urgent" message from your bank asking you to click a suspicious link, the fake Amazon notification with a dodgy sender address? Those days are long gone, along with the relevance of most of the advice we've been giving people about how to spot them.
Modern phishing attacks have evolved into something far more sophisticated and terrifying in their effectiveness. Let me walk you through how today's attackers actually operate – and why legacy advice might be doing more harm than good.
The New Phishing Playbook: It's Not About Fooling You Anymore
Attackers aren't really trying to trick you with clever emails anymore. Instead, they're playing a much longer, more strategic game that starts with compromising someone you actually know and trust.
Step 1: Getting That First Foothold
Today's attackers begin by compromising a real account – not by sending you a fake email, but by exploiting the weakest links in our digital lives - the supply chain:
- Password reuse (we've all done it – that same password from your old hotmail account that somehow made its way to three different work systems)
- Missing multi-factor authentication (yes, even in 2025, it's shocking how many accounts still don't have MFA enabled)
- Session token theft (those "remember me" cookies that keep you logged in can be stolen and replayed)
- Infostealer malware (malware that harvests your saved passwords and login tokens)
Once they're in one account, attackers don't immediately start asking for money or Bitcoin. They do something much smarter: they go shopping.
Step 2: The Reconnaissance Phase
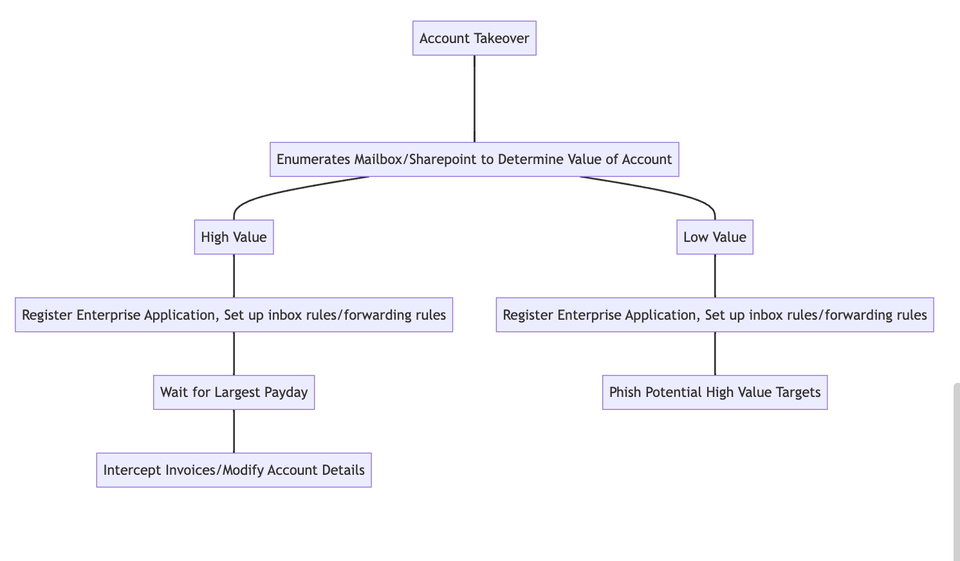
Attackers spend time digging through the compromised mailbox like they're conducting market research. They're looking for clues about whether they've hit the jackpot or just scored a minor win. I find it fascinating reviewing MailItemsAccessed when handling an incident. Tracking threat actor behaviour through a mailbox gives valuable insights into the motivation:
- What kind of company does this person work for?
- Do they handle invoices, payments, or procurement?
- Who do they email regularly, and what do those conversations look like?
- Are there any ongoing projects or vendor relationships they can exploit?
Based on what they find, attackers make a calculated decision about their next move.
The High-Value Target Route: Invoice Manipulation
If they've compromised someone with financial authority or access to business processes, attackers go for the big score. They don't just send a fake invoice – they become part of your business infrastructure:
- Installing enterprise applications that give them persistent access and the ability to monitor/backup communications
- Setting up inbox rules that automatically forward or hide specific emails (so when the real supplier asks why they haven't been paid, that email never reaches the victim)
- Intercepting and modifying real invoices by changing bank account details on legitimate transactions
Everything looks completely normal. The email comes from the right person, passes all SPF, DMARC and DKIM checks , the invoice looks identical to previous ones, and the only thing that's changed is where the money goes.
The Low-Value Target Route: Expansion Campaign
If the compromised account doesn't offer direct financial opportunities, attackers pivot to using it as a launching pad. They'll craft convincing phishing emails to the victim's contacts – and these emails are devastatingly effective because:
- They come from someone the recipients actually know and trust
- They reference real conversations, projects, or relationships
- They're sent at appropriate times and in the victim's usual communication style
I was once told by a previous employer who was truly gifted in the sales space that "Every dud knows a stud" - and this rings true for most businesses. A low value target will usually feature somewhere in the supply chain of much more profitable enterprise.
Why Traditional Advice Falls Short
All of this means that the security advice we've been giving people for years is not just outdated – it's potentially counterproductive.
"Only Trust Emails From Known Contacts" – Except When You Shouldn't
When the email genuinely comes from your colleague's account, this advice becomes useless. Worse, it creates false confidence. People see a familiar sender and let their guard down, never suspecting that the account has been compromised.
"Hover Over Links to See Where They Really Go" – Or Not....
Microsoft 365's SafeLinks feature (and similar services from other providers) means that hovering over a link shows you... Microsoft's URL rewriting service. The actual destination is hidden behind multiple redirects, making this technique completely ineffective for modern email systems.
"Look for the Padlock and Check for HTTPS" – Welcome to 2025
Setting up a legitimate-looking website with proper SSL certificates is trivially easy today. Attackers routinely use reverse proxy tools that show you legitimate login pages, complete with valid certificates and convincing URLs. That padlock isn't protecting you from phishing – it's just telling you the connection is encrypted.
So What Actually Works Now?
The shift we need to make is from "spotting bad emails" to "verifying unexpected requests." Instead of teaching people to be email detectives, we need to focus on:
- Out-of-band verification: If someone asks you to change payment details, call them. Not the number in the email – the number you already have.
- Process-based protections: Multi-person approval for financial changes, segregation of duties, and mandatory waiting periods for significant changes.
- Assumption of compromise: Planning for when (not if) accounts get compromised, with monitoring and rapid response capabilities.
Technical Controls That Actually Make a Difference
Beyond process changes, there are some technical measures that can significantly reduce your exposure to these evolved attacks:
Risky Sign-In Protection with Conditional Access
If you're using Microsoft 365 or Azure AD, enabling risky sign-in protection through Conditional Access policies is one of the most effective moves you can make. This system analyzes login attempts in real-time, looking for patterns that suggest compromise:
- Impossible travel scenarios (someone logging in from London and Brazil within an hour). Note that this will also flag in the event of commercial VPN use, but that's another conversation.
- Unfamiliar locations or devices that don't match the user's typical behavior
- Connections from known malicious networks
- Password spray attacks where the same password is tried across multiple accounts
When the system detects a risky sign-in, it can automatically block access, require additional authentication, or force a password reset. The beauty of this approach is that it works even when attackers have valid credentials – which, as we've established, they increasingly do.
Setting this up involves creating Conditional Access policies that trigger on medium or high-risk sign-ins. While it might seem like overkill, the reality is that legitimate users rarely trigger these conditions, but compromised accounts almost always do.
Phishing-Resistant MFA: Beyond SMS and App Notifications
Traditional MFA methods like SMS codes and push notifications are increasingly vulnerable to modern attack techniques. SIM swapping can bypass SMS, and "MFA fatigue" attacks can trick users into approving malicious login requests.
The solution is phishing-resistant MFA, which uses cryptographic methods that are virtually impossible to intercept or replay:
Passkeys are probably the most user-friendly option. They work like a more sophisticated version of your car's key fob – your device proves it has the right "key" without ever transmitting anything that could be stolen or replayed. They're built into most modern devices and browsers, so there's no additional hardware required.
Security keys like YubiKeys offer the gold standard for phishing resistance. These physical devices use FIDO2/WebAuthn protocols to provide cryptographic proof of identity. Even if an attacker manages to steal your username and password, they can't complete the login without physically possessing your security key.
The key advantage of both approaches is that they're "origin-bound" – they only work with the legitimate website or service. Even if an attacker creates a perfect phishing site, your passkey or security key will refuse to authenticate because it knows it's not talking to the real service.
For organizations, the migration path is straightforward: start by requiring phishing-resistant MFA for high-privilege accounts (admins, finance staff, anyone with access to sensitive systems), then gradually expand to all users. Most modern platforms support these methods, and the user experience is actually better than traditional MFA once people get used to it.
Principle of Least Privilege in 365 Accounts
Often we see accounts that have excessive permissions for their role. In on-premise infrastructure you used to often see staff with sysadmin roles having domain admin or enterprise admin group membership. Thankfully that's (mostly) now a thing of the past - but the lessons learned don't seem to have translated into Cloud environments, and I often see Exchange Admin or Global Admin permissions attached to mail-enabled accounts. Designate separate accounts for administrative functions.
TL;DR
Modern phishing isn't about fooling you – it's about becoming you, or at least becoming someone you trust. The attackers have moved beyond trying to craft the perfect deceptive email and instead focus on compromising real accounts and hijacking genuine relationships.
Our security advice needs to evolve accordingly. Instead of teaching people to spot fake emails, we need to help them verify real requests. The future of phishing defense isn't about training people to be suspicious of everything – it's about building systems and processes that remain secure even when trust is exploited.
Because in a world where attackers can literally send emails from your colleague or clients account about projects they're actually working on, suspicion alone isn't going to save us. We need to be smarter about how we verify, not just how we scrutinize.
